For detailed steps and configurations, follow along with the full video here.
Overview
This document provides the steps and configuration details for setting up a site-to-site VPN between an AWS VPC and an on-premises network using a Fortigate firewall.
Architecture
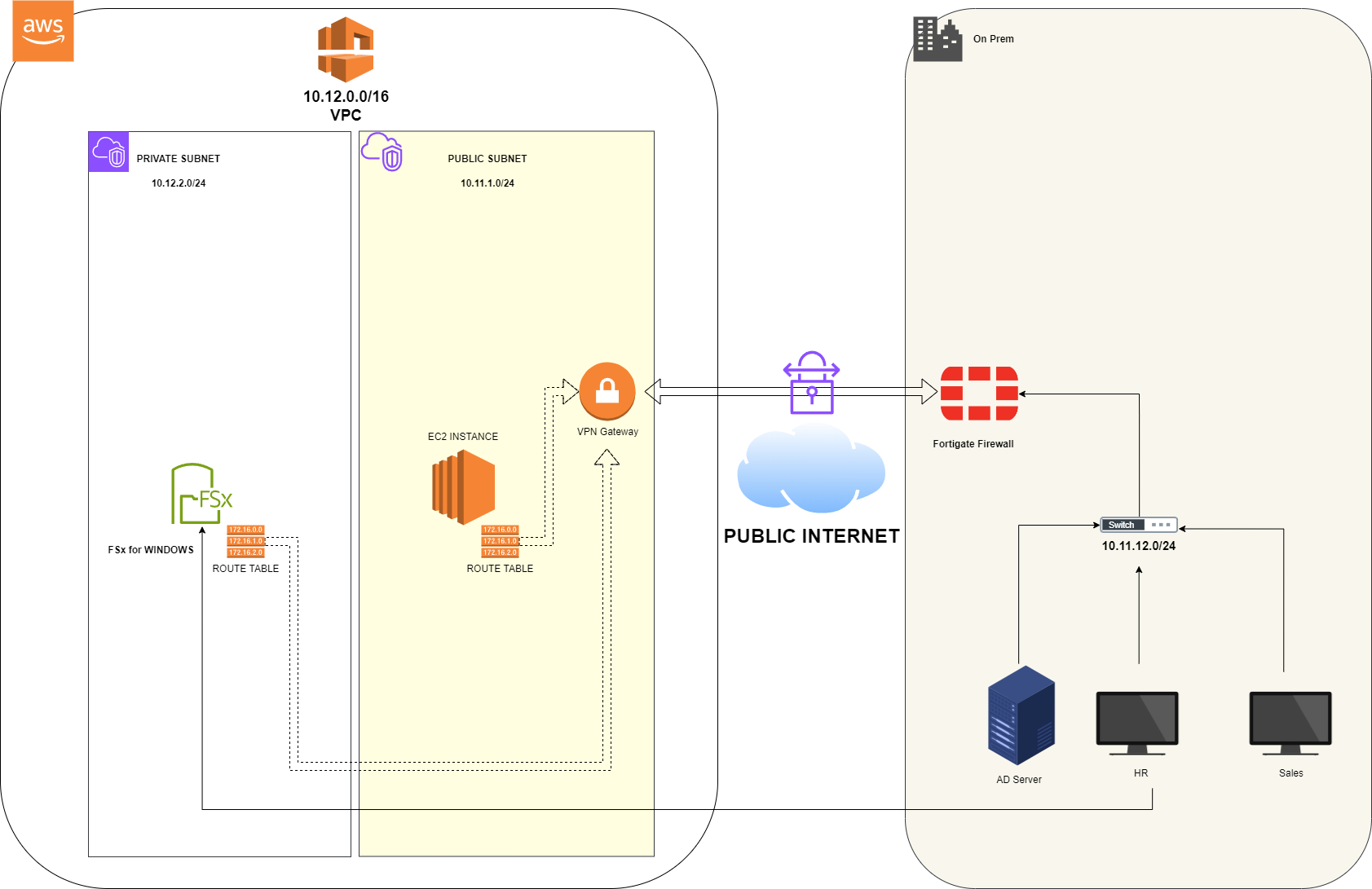
AWS Configuration
VPC Configuration
- VPC CIDR: 10.12.0.0/16
- Public Subnet CIDR: 10.12.1.0/24
- Private Subnet CIDR: 10.12.2.0/24
⚠️ IMPORTANT: Make sure that the CIDR doesn’t overlap with your on-prem network.
VPN Gateway
-
Create a Customer Gateway (CGW)
- Name:
On-Prem-CGW - IP Address:
<On-Premises Public IP> - BGP ASN:
65000
- Name:
-
Create a Virtual Private Gateway (VGW)
- Name:
AWS-VPG - Attach the VGW to the VPC (10.12.0.0/16)
- Name:
-
Create a Site-to-Site VPN Connection
- Name:
AWS-OnPrem-VPN - VPN Gateway:
AWS-VPG - Customer Gateway:
On-Prem-CGW - Routing Options: Static
- Static IP prefixes:
10.11.12.0/24 - Local IPv4:
10.11.12.0/24 - Remote IPv4:
10.12.0.0/16 - Download Configuration
- Follow the configuration notes
- Name:
Route Table Updates
- Update Route Table for Public Subnet
- Destination:
10.11.12.0/24 - Target:
AWS-VPG
- Destination:
On-Premises Configuration
Fortigate Firewall
-
Create a custom VPN
- Name:
AWS-VPN - Remote Gateway:
<AWS VPN Endpoint IP> - Pre-shared Key:
<Pre-shared Key from AWS>
- Name:
-
Configure Phase 1 and Phase 2
- Follow the configuration notes
-
Set an IP address for tunnel
- Set the IP address based on the configuration notes.
-
Create Static Routes
- Destination:
10.12.0.0/16 - Gateway:
AWS-VPG
- Destination:
Firewall Policies
-
Create Policies to Allow Traffic
- Incoming:
Local Network (10.11.12.0/24) - Outgoing:
AWS-VPN (10.12.0.0/16) - Source:
All - Destination:
All - Service:
All - NAT:
Disabled
- Incoming:
-
Clone and Reverse the 1st policy
- Enable the new policy
Verification
AWS
- Check VPN Connection Status
- Ensure the VPN status is
UPon the AWS Management Console.
- Ensure the VPN status is
On-Premises
-
Check VPN Tunnel Status
- Ensure the VPN tunnel is
UPon the Fortigate firewall.
- Ensure the VPN tunnel is
-
Ping Test
- From an EC2 instance, ping the firewall and vice versa.